Chip in supported systems to encrypt the data partitions of your hard drives. This allows you to extend the protection of BitLocker to incompatible and legacy Windows operating systems. Once BitLocker is enabled on your host system, and the drives prepared and encrypted, the only step required is creation of the virtual devices on the encrypted drive.
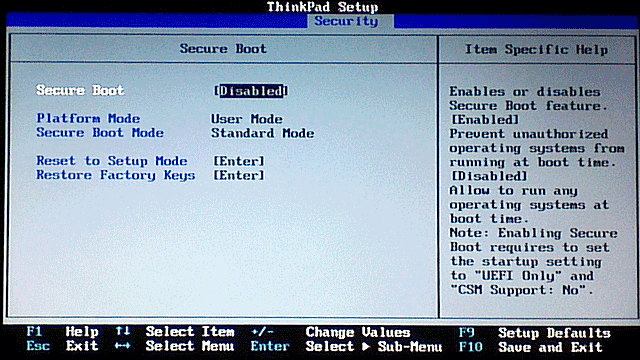
Secure Boot is a security standard developed by members of the PC industry to help make sure that your PC boots using only software that is trusted by the PC manufacturer. It is supported on modern versions of Windows, and many distributions of Linux and variants of BSD. When the PC starts, the firmware checks the signature of each piece of boot software, including firmware drivers and the operating system. If the signatures are good, the PC boots, and the firmware gives control to the operating system.1Secure Boot does not encrypt the storage on your device and does not require a TPM.
When Secure Boot is enabled, the operating system and any other boot media must be compatible with Secure Boot. The TPM also creates an Attestation Identity Key used to protect any changes to firmware and software. On each system boot, the system measurements will be compared with those stored in the TPM, and if there's a match the system will be considered trusted. Anyfailure in verifying the system integrity will result in locking the machine while stopping the boot process.
This way, if the machine has been manipulated, the TPM will be able to detect the manipulation without relying on the machine's own software. Microsoft currently requires all Windows 8 certified platform vendors to provide secure boot functionality. While this might work fine for Microsoft and Apple, free OS vendors are not happy.
Linux implementations, for example, often do not include signing. Obtaining and managing code certificates is difficult, if not impossible, for decentralized and underfunded coding operations. While this is not typically a big problem for business desktop and mobile computing devices, it can cause problems for more technical users. Further, it can possibly affect use of Linux-based appliances. Platform-specific specifications define what parts of the library are mandatory, optional, or banned for that platform; and detail other requirements for that platform.
Platform-specific specifications include PC Client, mobile, and Automotive-Thin.AlgorithmsSHA-1 and RSA are required. Triple DES was once an optional algorithm in earlier versions of TPM 1.2, but has been banned in TPM 1.2 version 94. Many other algorithms are also defined but are optional. It permits the ANDing and ORing of these authorization primitives to construct complex authorization policies. In a Secure Boot chain, each step in the process checks a cryptographic signature on the executable of the next step before it's launched. Thus, the BIOS will check a signature on the loader, and the loader will check signatures on all the kernel objects that it loads.
The objects in the chain are usually signed by the software manufacturer, using private keys that match up with public keys already in the BIOS. If any of the software modules in the boot chain have been hacked, then the signatures won't match, and the device won't boot the image. Beginning with power-up, all firmware is measured or signature-checked to ensure authenticity. Collections of pre-boot loader measurements can attest to the trusted state of a platform, alert administrators to potential issues, or block platform initialization.
How Do I Install Windows 11 Without Tpm And Secure Boot Boot loader signing prevents malicious takeover by ensuring only authorized boot components load. Finally, ELAM drivers verify the authenticity of third-party drivers and other software loading after the kernel but before user interaction. In the Microsoft model, firmware and the boot loader are integrity checked using signatures as well as measurements. The objective is to ensure all executables are signed and the signature public keys stored on the target platform in an "allowed database." .
Prior to boot loader execution, for example, its signature is checked, as shown in Figure 8-10. If the signature is invalid, the executable is managed according to user-defined policy. Finally, the UEFI is an independent operating environment that presents an API and services to BIOS firmware, third-party firmware, and the operating system. Taking charge of the boot path, the UEFI uses the TPM to measure the integrity of each firmware instance, device driver, or operating system module before it loads. When necessary, it also allows backward compatibility with traditional BIOS operations.
This establishes a strong root of trust before the user begins business processing. Each part checks the integrity of the following one by verifying the components digital signature. The certificates of image signers are verified using a public key stored as part of a root certificate issued by Microsoft. This certificate is hardcoded in the boot manager executable, the windows loader and the Windows kernel in a data structure informally referred to as the root table. They are most often referred to in the context of measured boot, i.e. secure measurements and attestation of all images in the boot chain. The TPM 2.0 specification defines versatile HSM devices which can also strengthen security of various other parts of your system.
We will describe the basic features of TPM and mention some caveats and shortcomings which may have contributed to its limited adoption. In addition to PCRs, module storage consists of VRAM and NVRAM (non-volatile memory) (Du, Li, & Shen, 2011). NVRAM contains hardware-protected root of trust data necessary to execute and assure boot path measurements. In addition, it contains certificates necessary for attestation of signed operating system files and firmware. Conversely, VRAM contains command parameters and is subject to operational changes.
The TrueCrypt disk encryption utility, as well as its derivative VeraCrypt, do not support TPM. As such, the condemning text goes so far as to claim that TPM is entirely redundant. The VeraCrypt publisher has reproduced the original allegation with no changes other than replacing "TrueCrypt" with "VeraCrypt".
The author is right that, after achieving either unrestricted physical access or administrative privileges, it is only a matter of time before other security measures in place are bypassed. However, stopping an attacker in possession of administrative privileges has never been one of the goals of TPM (see § Uses for details), and TPM can stop some physical tampering. The primary scope of TPM is to ensure the integrity of a platform. In this context, "integrity" means "behave as intended", and a "platform" is any computer device regardless of its operating system. This is to ensure that the boot process starts from a trusted combination of hardware and software, and continues until the operating system has fully booted and applications are running.
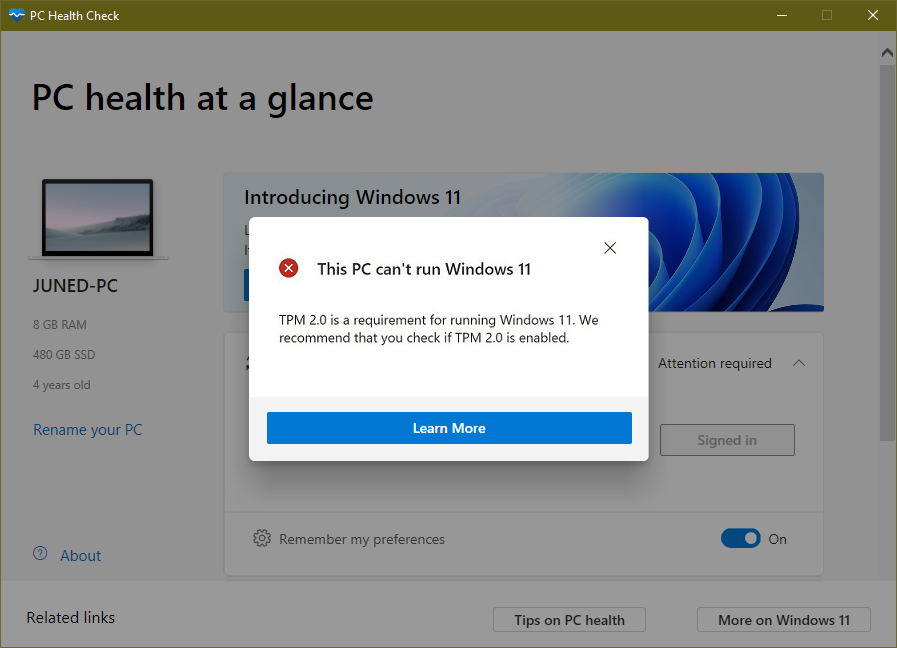
Trusted Platform Module 2.0 (TPM 2.0) and Secure Boot have both been around for a few years and most new Windows 10 computers will be running the security protocols by default. The technology combines special motherboard hardware in the form of chipsets with cryptographic security protocols to prevent malware from running before the Windows 10 operating system starts to boot. If you don't have access to the Windows 10 desktop, or this is a new computer, you can access the UEFI settings to enable a trusted platform module during the startup process. You wouldn't typically think about TPM on home devices since this was more a feature designed for businesses. However, Windows 11 is expected to start rolling out to devices sometime towards the end of the year, and Microsoft is now making the trusted platform module a prerequisite to install the OS.
Secure Boot and Measured Boot with Intel® TXT share the same primary goal. They aim to validate that there have been no unauthorized changes to critical parts of the platform code, in order to provide a secure environment for applications. In order to do this, they both rely on the Root of Trust to build a Chain of Trust during a platform boot process so the users may have confidence in a secure environment. In both scenarios, the TPM is used as a cryptographically secure place to store measurements of trust, though Secure Boot only uses it for an enabled flag. Both technologies can and should be used at the same time.
The first time you boot a VM instance, Measured Boot creates the integrity policy baseline from the first set of these measurements, and securely stores this data. Each time the VM instance boots after that, these measurements are taken again, and stored in secure memory until the next reboot. Having these two sets of measurements enables integrity monitoring, which you can use to determine if there have been changes to a VM instance's boot sequence. Measured Boot enhances boot security by storing measurements of boot components, such as bootloaders, drivers, and operating systems. The first time you boot a shielded instance, Measured Boot uses the initial measurements to create a baseline. The baseline measurements are also known as golden measurements.
Each of these components, or component groups, plays an important UEFI support role. The RSA Engine can create one-time symmetric keys of up to 2048 bits. It is used during key wrapping operations, digital signing, and encrypting large blocks of data.
The SHA-1 (or SHA-256) engine hashes large blocks of data. RNG is a module's random number generator used to generate keys. The AIK is bound to the platform on which the module resides. It is an asymmetric key pair that attests to the validity of the platform's identity and configuration.
There are 24 Platform Configuration Registers , many of which are used to store measures created during the UEFI boot process. Microsoft has a habit of struggling to move Windows into the future in both hardware and software, and this particular change hasn't been explained well. While Microsoft has required OEMs to ship devices with support for TPM chips since Windows 10, the company hasn't forced users or its many device partners to turn these on for Windows to work. That's what's really changing with Windows 11, and combined with Microsoft's Windows 11 upgrade checker, it has resulted in a lot of understandable confusion.
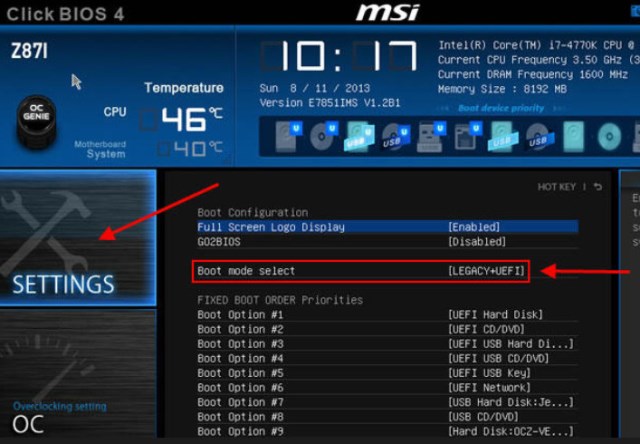
When enabled and fully configured, Secure Boot helps a computer resist attacks and infection from malware. Secure Boot detects tampering with boot loaders, key operating system files, and unauthorized option ROMs by validating their digital signatures. Detections are blocked from running before they can attack or infect the system. Click the Troubleshoot option, then Advanced Options, and select the option for UEFI Firmware Settings.
This will then prompt you to restart the system, but rather than booting straight to desktop, it will instead enter the system UEFI. According to Microsoft, one of their primary concerns was with malware attacks that specifically targeted system vulnerabilities which are present prior to an OS fully initialising. As such, by enabling these new security features, it would be possible to mitigate these weaknesses by locking down the very hardware on which the OS is installed. (usually built into the system/motherboard), which stores the encryption/decryption keys and releases them only after verifying the integrity of early boot components and boot configuration data.
In short, the practical effect is that the TPM will allow a BitLocker-encrypted drive to be booted only if the drive is located in its original computer. BitLocker and its TPM can also work in conjunction with a PIN and/or a USB device containing the required keys. It serves as the first verification performed in the system, in which the basic characteristics of the system are verified. Moreover, the TPM verifies that the BIOS can be trusted, in which case it passes control to it. You can enable BitLocker for Windows boot disks that are part of Shielded VM images. Shielded VM images offer security features such as UEFI-compliant firmware, Secure Boot, vTPM-protected Measured Boot, and integrity monitoring.
VTPM and integrity monitoring are enabled by default, and Google recommends enabling Secure Boot if possible. Early boot is the boot sequence from the start of the UEFI firmware until it passes control to the bootloader. Late boot is the boot sequence from the bootloader until it passes control to the operating system kernel. If either part of the most recent boot sequence doesn't match the baseline, you get an integrity validation failure.
Updating Forbidden Signatures Databases on shielded VM instances is not supported. A DBX maintains a secure boot database of signatures that are not authorized to run on the platform. Applying DBX updates on a shielded VM instance might prevent the instance from booting. To update the DBX, create a new shielded VM instance with an image that includes the DBX updates. Secure Boot is a Unified Extensible Firmware Interface feature that prevents unauthorized boot loaders and operating systems from booting. Secure Boot validates that the signed firmware's signature is correct before booting to prevent rootkits, bootkits, and unauthorized software from running before the operating system loads.
Boot components that aren't properly signed are not allowed to run. UEFI benefits extend beyond memory and compatibility improvements. Limitations in MBR-based boot processes are resolved with the UEFI's use of the GUID Partition Table . The GPT uses globally unique identifiers to address partitions, allowing booting from disks as large as 9.4 ZB [9.4 x 1021 bytes] . Further, the UEFI allows more platform boot options, including network boot capabilities, and can act as the foundation for extended boot loaders. Storage limitations disappear, and boot processes can retrieve data and program modules from anywhere on installed storage.
These types of attacks can destroy the integrity of one or more platforms across an organization. It is crucial that when the user login prompt appears, the system is trusted and safe for sensitive information and critical business processes. This starts by establishing a root of trust with the TPM as its support.
Windows Security Center can be accessed in Windows 10 by searching for it in the Start Menu. When open, you can check under Virus and Threat Protection to see any threats or start a scan. Microsoft always updates the security intelligence in Windows Security Center, to ensure you're protected against the latest threats. You'll also be able to turn on real-time protection to ensure that downloaded malware won't run, and cloud-delivered protection to ensure that you get faster protections. You even can turn on controlled folder access to make sure that if your PC is hijacked by ransomware, critical folders won't be available for the ransomware itself. In 2011, Microsoft announced that Secure Boot would be mandatory for Windows 8.
The outcry in the open source community was massive, because with Secure Boot it is possible to control which operating systems can be started on a PC. 10 years later, tempers have calmed down, because it is clear to everyone that IT security can only be achieved through trustworthy hardware and software . And Secure Boot, sometimes also called "Verified Boot" or "Trusted Boot", is a building block for this.
Under this setting should be an option to update the BIOS. Select this option and press enter, which should then prompt you to choose the drive with the files you'd like to install , then the file itself. Provided you have used a blank thumb drive, you should only have one option to select here. If the failure is expected, for example if you applied a system update on that VM instance, you should update the integrity policy baseline. Updating the integrity policy baseline sets the baseline to the measurements captured from the most recent boot sequence.
If it is not expected, you should stop that VM instance and investigate the reason for the failure. A vTPM is a virtualized trusted platform module, which is a specialized computer chip you can use to protect objects, like keys and certificates, that you use to authenticate access to your system. The Shielded VM vTPM is fully compatible with the Trusted Computing Group library specification 2.0 and uses the BoringSSL library. The BoringSSL library relies on the BoringCrypto module. For FIPS details about to the BoringCrypto module, see NIST Cryptographic Module Validation Program Certificate #3678.


























No comments:
Post a Comment
Note: Only a member of this blog may post a comment.